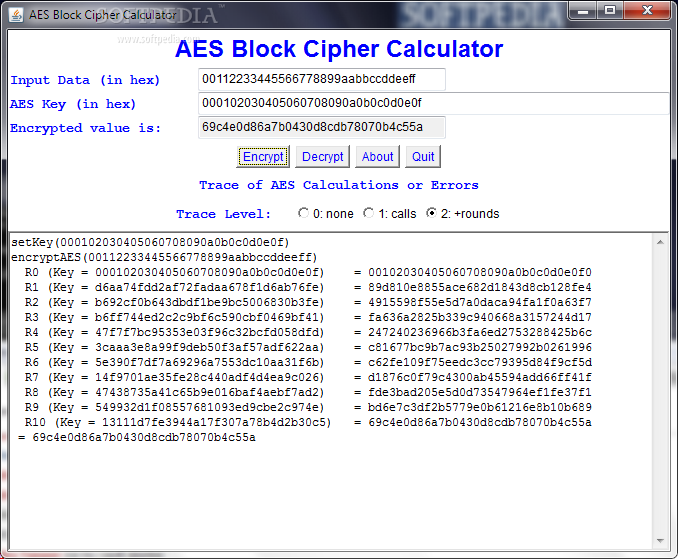
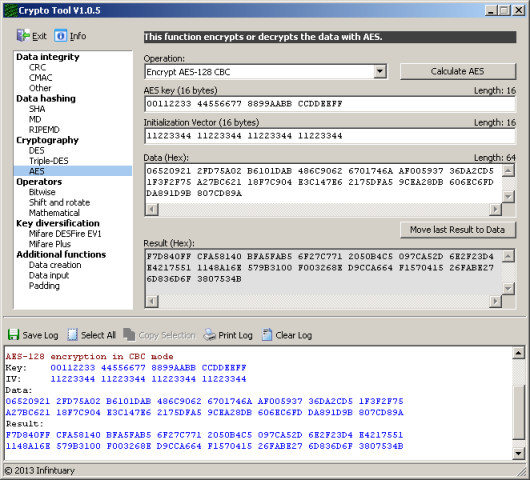
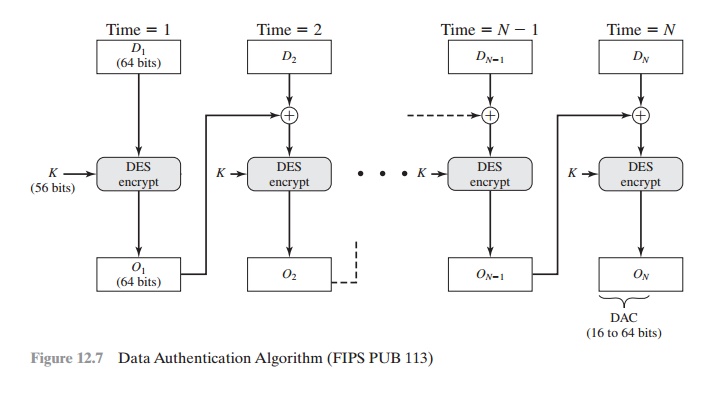
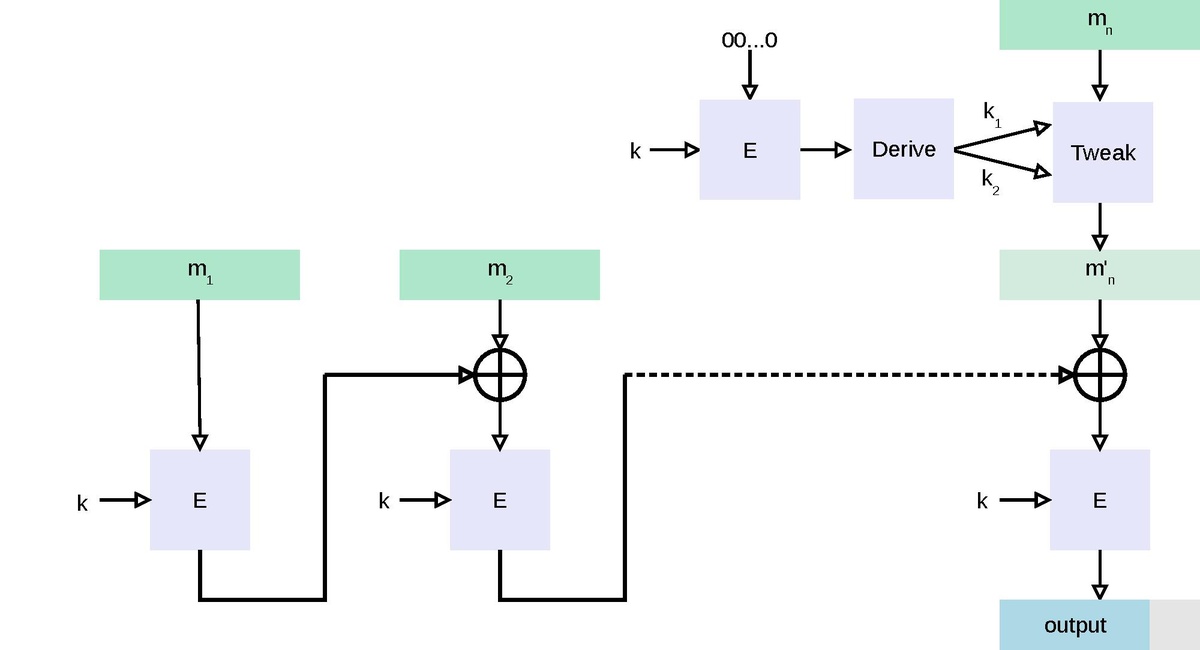
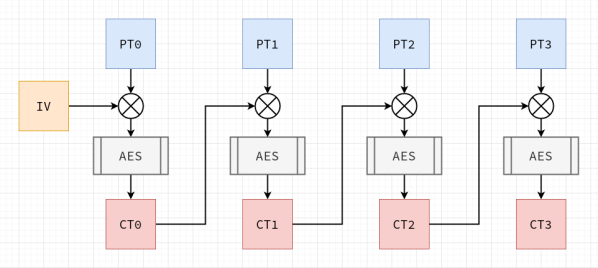
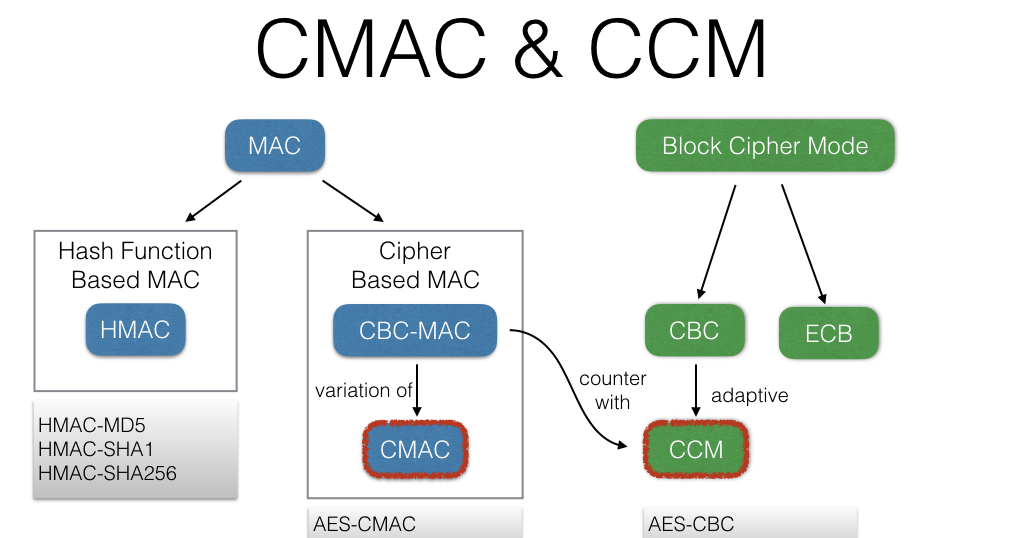
GitHub - chmike/cmac-go: Cipher-based Message Authentication Code as described in RFC4493 and NIST 800-38B
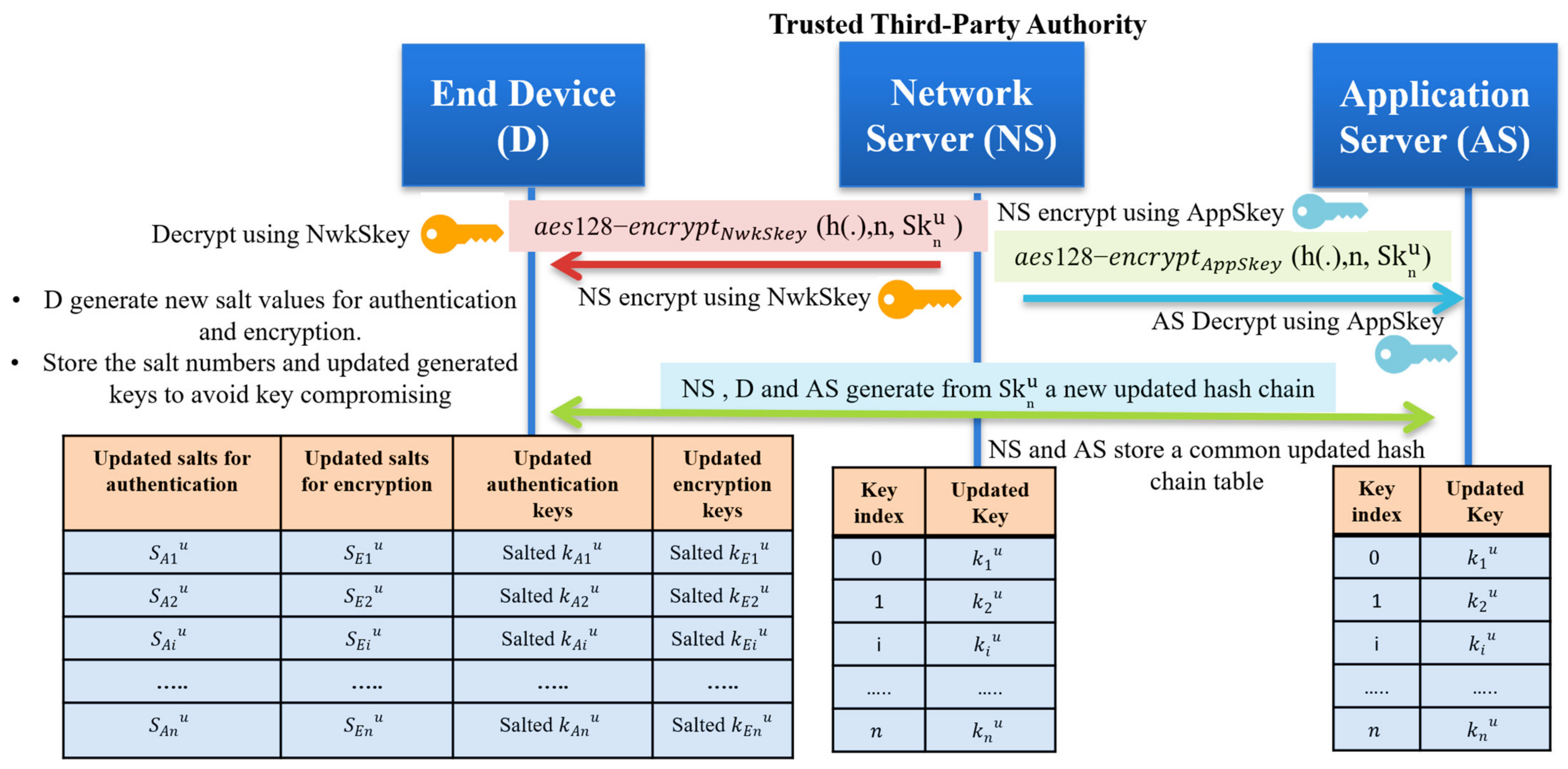
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks
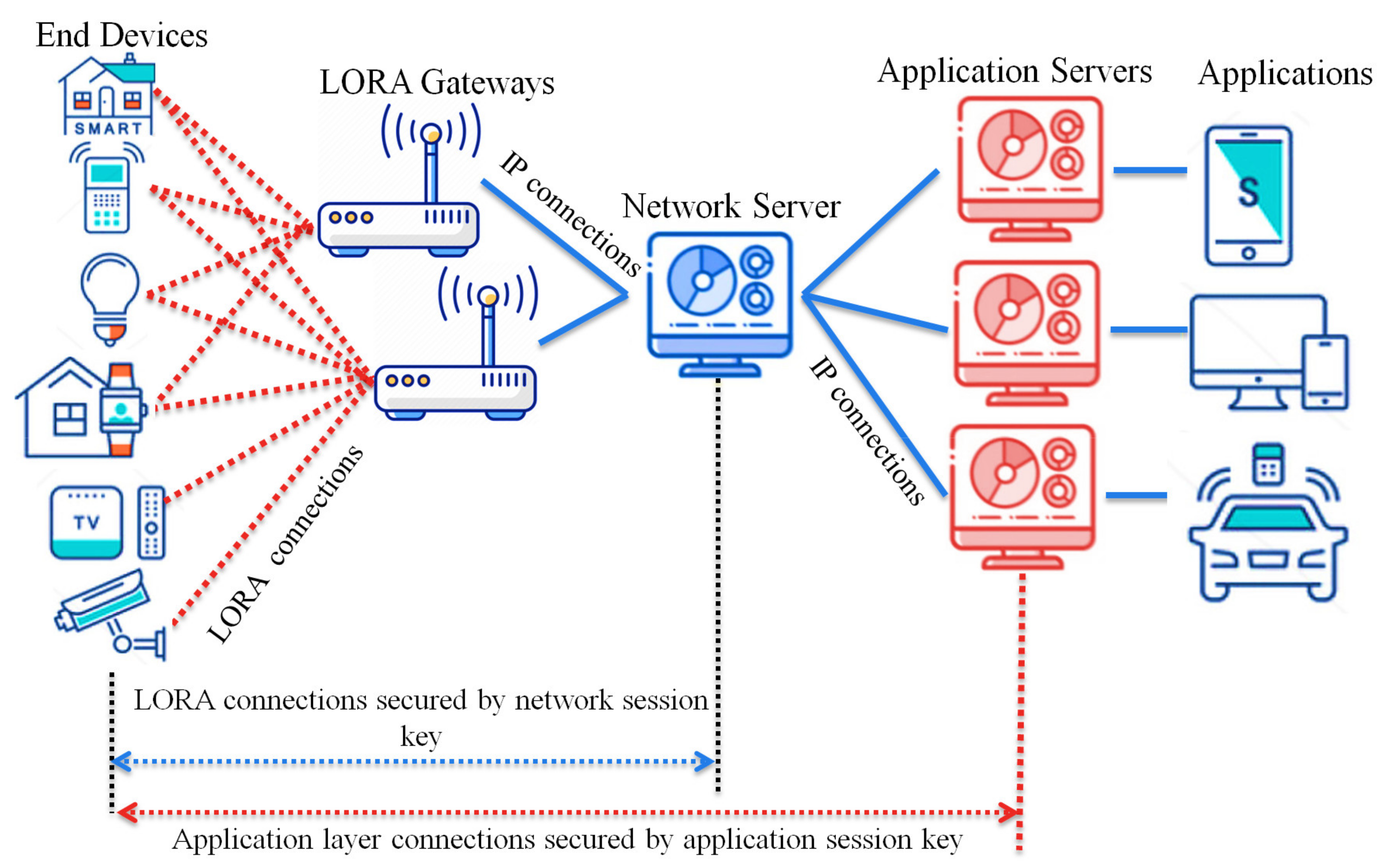
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks


![Research needed] Handling .cmd CMACs on SD card · Issue #340 · d0k3/GodMode9 · GitHub Research needed] Handling .cmd CMACs on SD card · Issue #340 · d0k3/GodMode9 · GitHub](https://user-images.githubusercontent.com/35666439/55014213-effa8a80-4fc0-11e9-82c2-bfd61a3cf91f.png)
![Research needed] Handling .cmd CMACs on SD card · Issue #340 · d0k3/GodMode9 · GitHub Research needed] Handling .cmd CMACs on SD card · Issue #340 · d0k3/GodMode9 · GitHub](https://user-images.githubusercontent.com/35666439/55248846-0737b300-5221-11e9-9aad-858f69b2663e.png)